Встроенный антивирус Exchange mail flow breaks (Disable AntiMalwareScanning)
Настройка встроенного антивируса
Для того,
чтобы встроенный антивирус забирал обновления с правильного URL по HTTPS, нужно
выполнить команду ниже. При необходимости можно так же настроить частоту
обновления и время ожидания. Не забудьте предоставить соответствующие сетевые
доступы.
Set-MalwareFilteringServer
EXCH19 -PrimaryUpdatePath https://forefrontdl.microsoft.com/server/scanengineupdate/ -UpdateFrequency 120 -DeferWaitTime
10
В случае необходимости отключения встроенного антивируса –
можно для начала проверить, что встроенный агент включен (Malware Agent - True), командой:
Get-TransportAgent
При
необходимости выключить скриптом:
C:\Program
Files\Microsoft\Exchange Server\V15\scripts>.\Disable-AntimalwareScanning.ps1
https://serverfault.com/questions/1085840/exchange-2019-antimalware-engine-updates-download-but-dont-get-applied
https://techcommunity.microsoft.com/discussions/exchange_general/exchange-20162019-filtering-engine-updates-failing-since-1272021/3037138
https://www.alitajran.com/exchange-mail-flow-breaks/
Exchange mail flow breaks (Disable AntiMalwareScanning)
Mail flow seems not to be working and the mail queue is getting bigger. If you see these issues, disable AntiMalWareScanning for now on the on-premises Exchange Servers and restart the Microsoft Exchange Server Transport Service.
Update: Microsoft releases a patch. See the part Solution to Exchange mail flow breaks.
Table of contents
Introduction
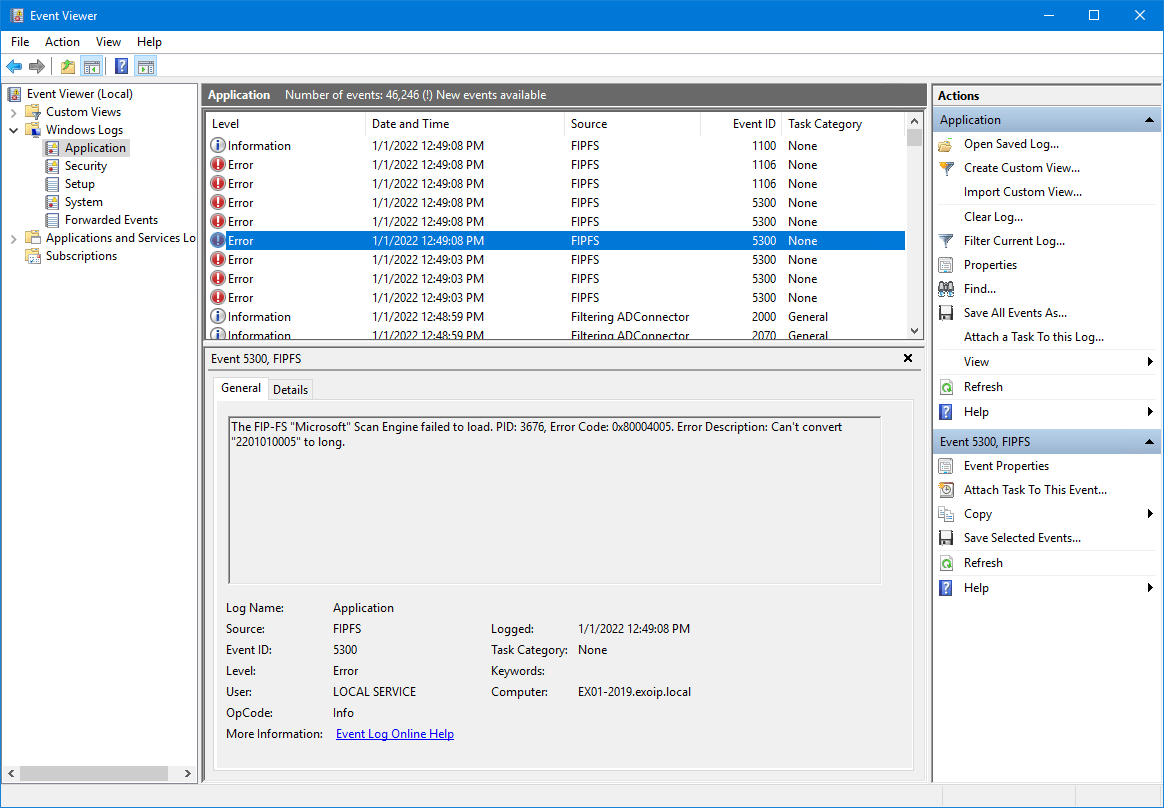
The mail flow is not working and you can check the error in Event Viewer.
Error
The FIP-FS “Microsoft” Scan Engine failed to load. PID: 9244, Error Code: 0x80004005. Error Description: Can’t convert “2201010005” to long.
Get mail queue
Run Exchange Management Shell as administrator and check the queue.
MICROSOFT RELEASED A PATCH FOR THE EMAIL STUCK IN TRANSPORT QUEUE. SKIP TO THE SOLUTION DOWN BELOW!!
Fix for Exchange mail flow breaks
There are two ways to fix the Exchange mail flow:
- Disable anti malware scanning (1a+2a)
- Bypass anti malware filtering (2a+2b)
Both methods will work. Choose one of these options and follow the steps below.
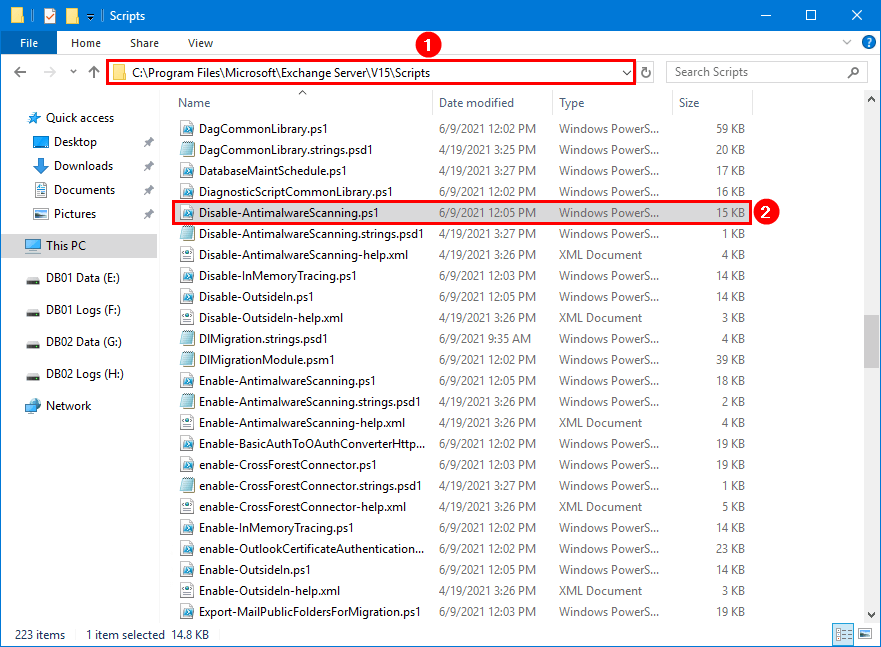
1a. Disable AntiMalWareScanning
In Exchange Management Shell, run the command to disable AntiMalware Scanning on the Exchange Server on-premises.
Note: This command can take a minute or more. Leave it running till it’s successfully run.
Note: To re-enable malware filtering, use Enable-Antimalwarescanning.ps1 instead of Disable-Antimalwarescanning.ps1.
You can find the script Disable-AntiMalWareScanning.ps1 in File Explorer.
1b. Bypass anti malware filtering
In Exchange Management Shell, run the command to bypass anti malware filtering on the Exchange Servers on-premises.
2a. Verify AntiMalwareScanning is disabled
To verify that malware filtering is disabled, run the Get-TransportAgent cmdlet and confirm that it returns a value of False.
2b. Verify bypass filtering is disabled
To verify that malware bypass filtering is disabled, run the Get-MalwareFilteringServer cmdlet and confirm that it returns a value of True.
3. Restart Exchange Server Transport Service
Restart the Microsoft Exchange Server Transport service.
Restart the Microsoft Exchange Server Transport service on all Exchange Servers.
Read more: Restart Exchange Server services through PowerShell »
The queue will start to process the mail.
Solution to Exchange mail flow breaks
Microsoft did release a patch and you can run that in your environment.
Implementation of the solution requires customer actions. These actions can be automated with the scan engine reset script from https://aka.ms/ResetScanEngineVersion or they can be performed manually.
Important: Whether you perform the steps automatically or manually, they must be performed on every Exchange 2016 and Exchange 2019 server in your organization.
If you use the automated script, you can run it on multiple servers in parallel. We recommend starting with the servers in your environment that have the largest queues. You can use Get-Queue to view queue size and determine which queues are the largest.
Note: If you previously disabled or bypassed antimalware scanning as a mitigation for this issue, we recommend that you re-enable it after performing the steps below.
1a. Automated Solution
Download the ResetScanEngineVersion.ps1 PowerShell script and place it on the Exchange Server C:\scripts folder. If you don’t have a scripts folder, create one.
- Run Exchange Management Shell as administrator
- Run Set-ExecutionPolicy -ExecutionPolicy RemoteSigned
- Change the path to the scripts folder
- Run the script .\ResetScanEngineVersion.ps1
Important: Run the .\ResetScanEngineVersion.ps1 PowerShell script on each Exchange Server.
Run the script on each Exchange server in your organization. You can run this script on multiple servers in parallel. After the script has completed, you will see the following output:
Note: Do you get the error “Cannot stop process” in relation to the updateservice.exe located in the FIP-FS? Ensure that the account you sign in to the Exchange Server has Debug programs user rights under the Local Group Policy. Otherwise, the process will not terminate, and the script fails to run.
1b. Manual Solution
You can can also manually perform steps to resolve the issue and restore service. To manually resolve this issue, you must perform the following steps on each Exchange server in your organization:
Remove existing engine and metadata
- Stop the Microsoft Filtering Management service. When prompted to also stop the Microsoft Exchange Transport service, click Yes.
- Use Task Manager to ensure that updateservice.exe is not running.
- Delete the following folder: %ProgramFiles%\Microsoft\Exchange Server\V15\FIP-FS\Data\Engines\amd64\Microsoft.
- Remove all files from the following folder: %ProgramFiles%\Microsoft\Exchange Server\V15\FIP-FS\Data\Engines\metadata.
Update to latest engine
- Start the Microsoft Filtering Management service and the Microsoft Exchange Transport service.
- Open the Exchange Management Shell.
- Navigate to the Scripts folder (%ProgramFiles%\Microsoft\Exchange Server\V15\Scripts).
- Run .\Update-MalwareFilteringServer.ps1 <server FQDN>
2. Verify engine update info
- Start Exchange Management Shell.
- Run Add-PSSnapin Microsoft.Forefront.Filtering.Management.Powershell.
- Run Get-EngineUpdateInformation and verify the UpdateVersion information is 2112330001 or higher.
Note: Run the Get-EngineUpdateInformation cmdlet and verify the UpdateVersion information is 2112330001 or higher.
Filter the Application log on the Event sources: FIPFS.
3. Re-enable anti malware scanning
If you did apply the fix before that Microsoft published a solution, enable anti malware scanning. If you did not apply any fix and you immediately applied the solution, you don’t have to re-enable anti malware scanning because it’s enabled by default.
Did you disable anti malware scanning? Run the command below and restart the Microsoft Exchange Transport Service.
Did you bypass anti malware scanning? Run the command below and restart the Microsoft Exchange Transport Service.
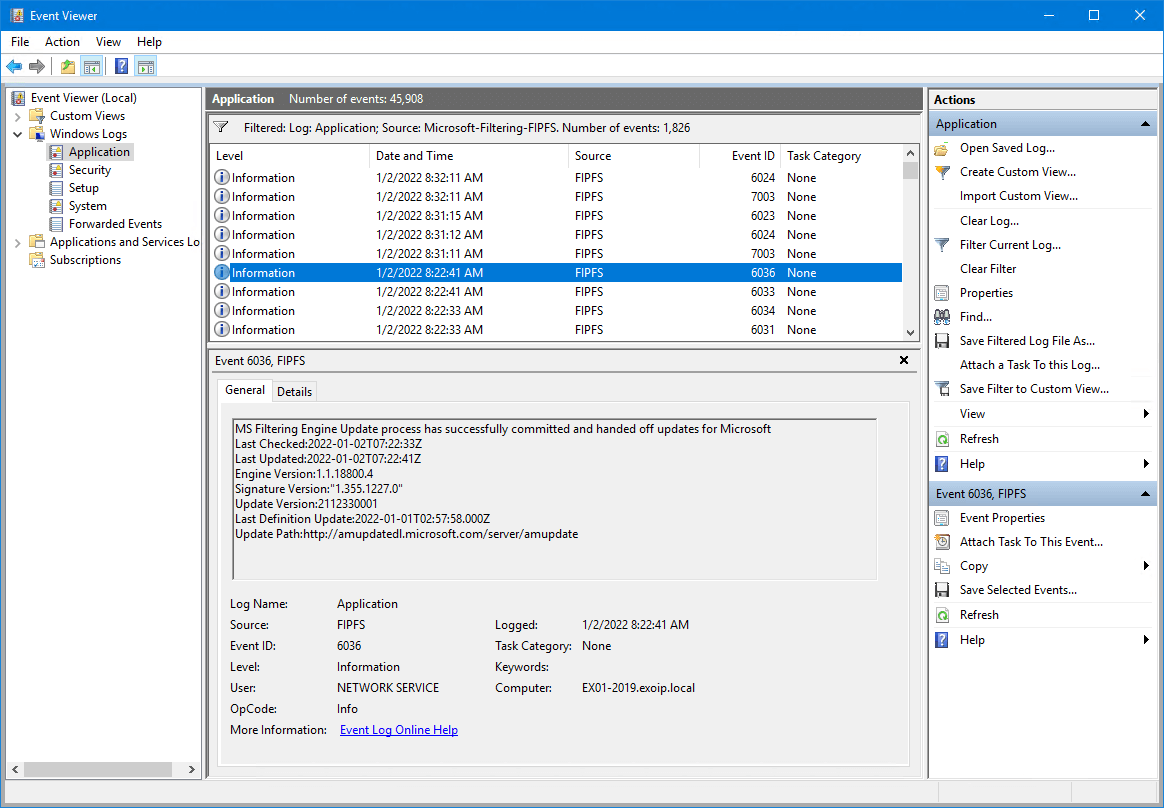
4. Verify mail flow and FIPFS error events not present
After updating the engine, we also recommend that you verify that mail flow is working and that FIPFS error events are not present in the Application event log.
Test and verify that mail flow works:
- Test internal mail flow in Exchange Server
- Test inbound mail flow in Exchange Server
- Test outbound mail flow in Exchange Server
Important: Do you see FIPFS errors in the event log and the email are still stuck in the queue/mail flow is not working after running the ResetScanEngineVersion.ps1 PowerShell script? RESTART THE EXCHANGE SERVER.
Latest updates
Update: Microsoft pushed an agent update, but it’s not yet working. So keep anti-malware scanning disabled.
Update1: Updated screenshot with how to check the event viewer for the issue.
Update2: Downloaded the latest MS Filtering Engine Update: Update Version:2201010006, it’s still not working.
MS Filtering Engine Update process has successfully committed and handed off updates for Microsoft
Last Checked:2022-01-01T12:05:10Z
Last Updated:2022-01-01T12:05:18Z
Engine Version:1.1.18800.4
Signature Version:”1.355.1234.0″
Update Version:2201010006
Last Definition Update:2022-01-01T05:20:29.000Z
Update Path:http://amupdatedl.microsoft.com/server/amupdate
Update3: Added both the options on how to disable anti malware scanning or bypass anti malware filtering.
Update4: MS Filtering Engine update will not fix this issue. You don’t have to check for engine updates. Implement this fix and wait for a proper fix release by Microsoft.
Update5: Microsoft Product Manager sent me a message, and they are working on a fix. The fix will be released with how-to instructions. Stay tuned.
Update6: You can wait for the Microsoft patch if you have enough disk space and don’t mind that Exchange Server will deliver the messages later. If not, apply the fix and patch later when Microsoft releases.
Update7: Microsoft Exchange Server expiration message is by default 48 hours (2 days). If a message remains in the queue for longer than this period of time, the message is returned to the sender as a permanent failure.
You can change that value between 1-90 days. The problem is that the longer days you set, the more messages will stay, the larger the mail queue will become. It means you have to keep adding more disk space.
I recommend running the above fix. But, if you do not want to disable the anti malware scanning, it’s better to expand the message expiration timeout in the Transport Server. Just to be safe.
In the example below, it’s 2 days.
Change it to 4 days (or another value).
Update8: Microsoft patch is OUT! Run the automated or manual solution. I recommend the automated solution first.
Update9: If you applied the fix before the solution, don’t forget to re-enable antimalware scanning and restart the Microsoft Exchange Transport Service.
Update10: Updated screenshot with how to check the event viewer after applying the solution.
Update11: The mail.que database got larger in size, and it will not shrink automatically. This happened because the Exchange Server kept the mail in the queue, and the messages didn’t get released before the fix/solution. It can take a lot of space, and I recommend making it smaller by removing the mail.que database. After that, Exchange Server will automatically create a new mail.que database.
Read more: Mail.que file large in size Exchange Server »
Update12: If you didn’t have enough disk space on the OS drive or ran out of disk space because of the mail.que database was filling up, it’s now an excellent time to move the mail.que database to another drive. This way, the OS drive will stay active and not give you performance issues.
Read more: Move mail queue to another location in Exchange Server »
Update13: Added articles to test mail flow internal/inbound/outbound.
Update14: Some admins mention that an Exchange Server reboot is required after applying the Solution. After that, the mail queue gets empty/mail flow starts working.
Update15: Running the Update-MalwareFilteringServer.ps1 cmdlet shows: Error starting the anti-malware engine update. To fix this error, run the steps below:
- Run Exchange Management Shell as administrator
- Run Add-PSSnapin Microsoft.Forefront.Filtering.Management.Powershell
- Run Start-EngineUpdate
- Run Get-EngineUpdateInformation
Update 16: Only Exchange Server 2016 and Exchange Server 2019 are affected. The Exchange Edge Transport server is not affected by this Microsoft Exchange Y2K22 bug.
Update 17: UpdateVersion is now on 2112330003. Added to the article that it needs to show UpdateVersion 2112330001 or higher.
Update 18: Some admins mention that Exchange Server 2013 is also affected and some say it’s not. This is not true and the mail transport will work. But, you have to run the same script automatically or manually.
If your Exchange 2013 server took the antimalware update and it is now on version starting with “22…” you should use the automated or manual steps in this blog post to get your server on an engine version “21…” to continue getting the antimalware updates. Without taking action your server will not get any future antimalware updates.
Update19: Added to run Set-ExecutionPolicy -ExecutionPolicy RemoteSigned in Exchange Management Shell before running the script.
Update20: The definition download takes 30-45 minutes (maybe slower depending on Internet speed), so allow for some time.
Update21: Added solution to updateservice.exe access denied error when running the script.
Subscribe to the newsletter and stay up to date with the latest IT tips and tricks.
Did this article help you? Share this article with your network and help them too.

Комментарии
Отправить комментарий