Create Exchange Server reCAPTCHA
https://www.alitajran.com/protect-exchange-owa-ecp-brute-force-attacks/
Protect Exchange Server OWA/ECP from brute force attacks
A lot of bots attack the Exchange Server OWA and ECP page constantly. It’s the (security) engineers task to secure and protect the Exchange Server OWA/ECP URLs from attacks. Measures such as Multi-Factor Authentication (MFA) or only making the OWA/ECP accessible through VPN are excellent ideas. Another method to stop Exchange Server brute force attacks is integrating Google reCAPTCHA to the OWA/ECP page. It’s FREE and works excellently.
Table of contents
Protect Exchange Server OWA/ECP from attacks
There are a lot of methods to protect Exchange Server OWA/ECP from attacks. Here are the best ones to protect Exchange Server OWA/ECP from brute force attacks:
- Configure a third-party MFA solution
- Configure VPN so only users connected to the internal network can access Exchange OWA/ECP
- Enable selected countries only in the firewall that can access Exchange OWA/ECP
- Configure Azure app proxy (Azure AD Premium P1 or P2 license)
If you don’t want to spend money on an MFA solution or you don’t want to pay Azure AD Premium P1 or P2 license, you can protect Exchange OWA/ECP from brute force attacks by adding a reCAPTCHA in the sign-in page.
Exchange Server Google reCAPTCHA integration
To create a Google reCAPTCHA site and integrate it into Exchange Server OWA/ECP, go through the below steps:
Create Google reCAPTCHA site
The first step is to create a new Google reCAPTCHA site. Once we have the reCAPTCHA keys, we can integrate them into Exchange Server.
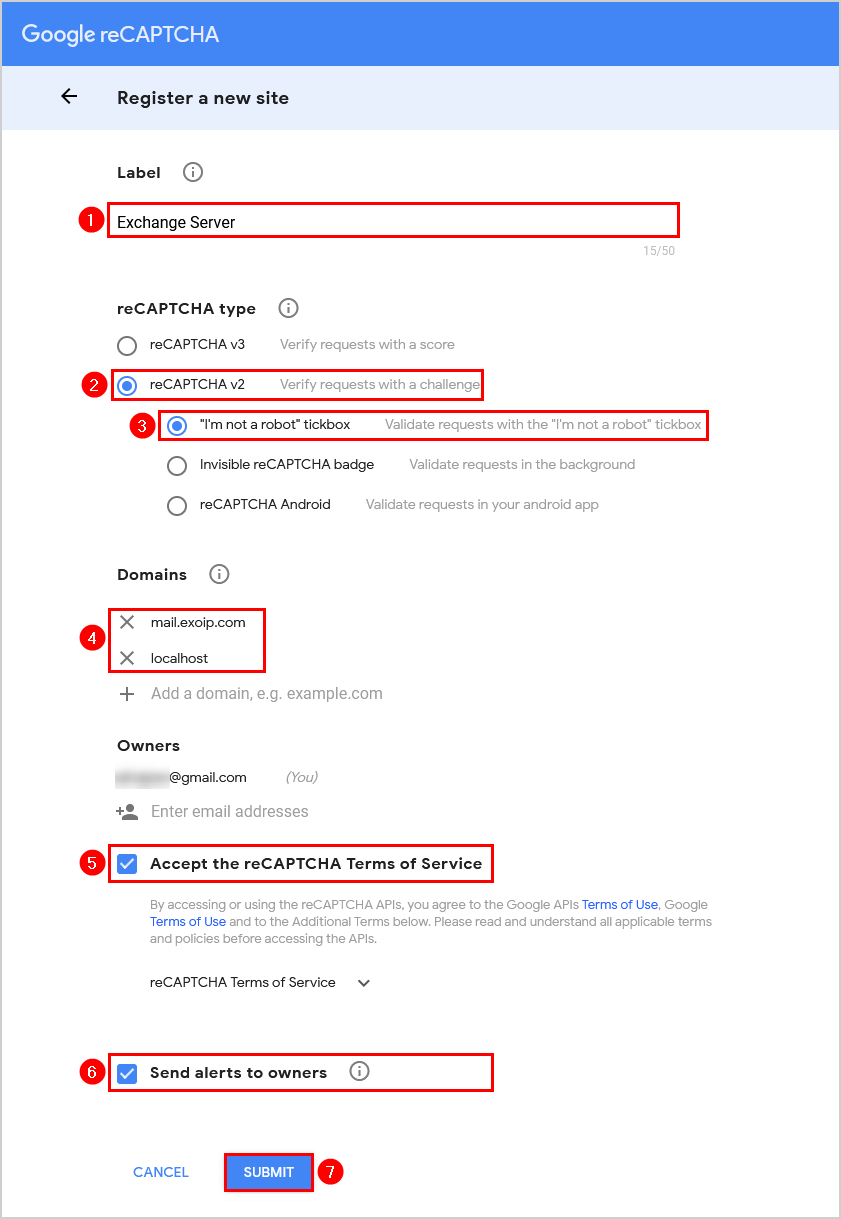
Sign in to Google reCAPTCHA and fill in the below details:
- Label: Exchange Server
- reCAPTCHA type: reCAPTCHA v2 – “I’m not a robot” tickbox
- Domains: mail.exoip.com (your Exchange URL) and localhost
Check both the checkboxes:
- Accept the reCAPTCHA Terms of Service
- Send alerts to owners
Click on Submit.
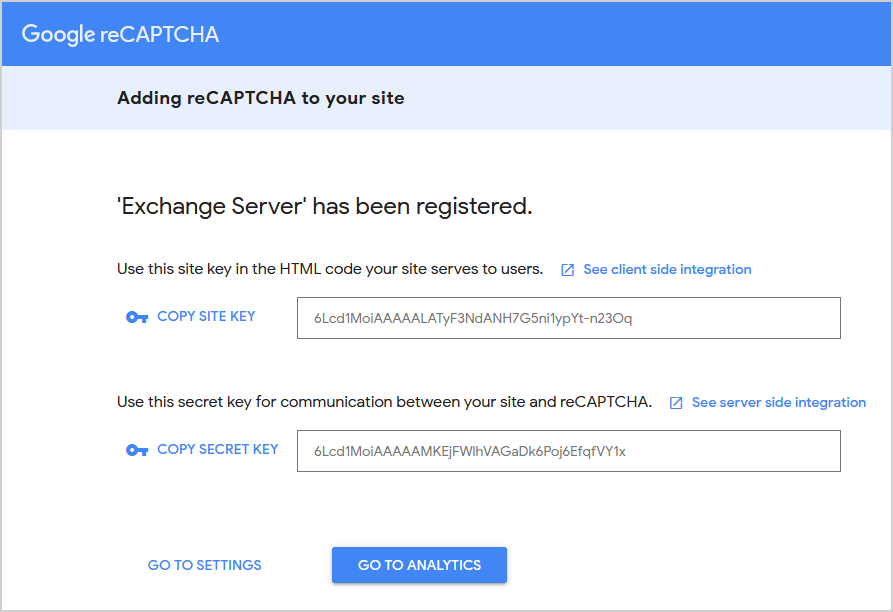
The site key and secret key will appear. Copy both keys and save them because you need them in the next step.
Create Exchange Server reCAPTCHA page
Let’s integrate the site key into Exchange Server.
Note: Do the below steps on every Exchange Server (CAS).
Sign in to the Exchange Server and go to the below path. Suppose you have an older Exchange Server version, change V15 to another version. For example, V14.
Create a new file with Notepad with the name recaptcha.aspx in that folder.
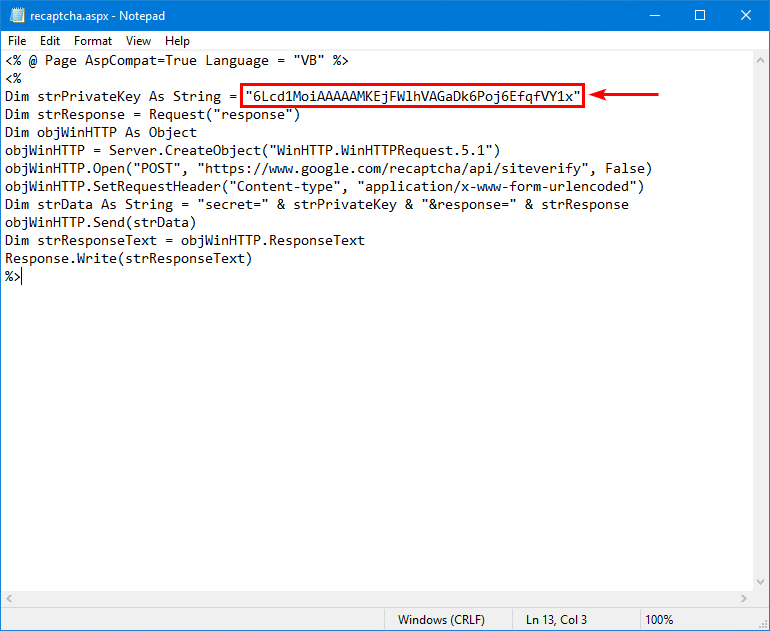
Copy/paste the below information into it.
Paste the Google reCAPTCHA secret key you copied in the previous step and paste it in the field SECRET_KEY.
Configure Exchange Server OWA/ECP logon page
Let’s integrate the secret key into Exchange Server.
Make a backup of the logon.aspx file, just in case you have to revert the changes. Copy logon.aspx and rename it to logon.aspx.bak.
Note: The file logon.aspx will be rewritten to its original state when you install Exchange Server CU. So write down in your manual to replace the file after the CU and test that the Google reCAPTCHA works.
Open the logon.aspx file with Notepad and modify the below:
Find:
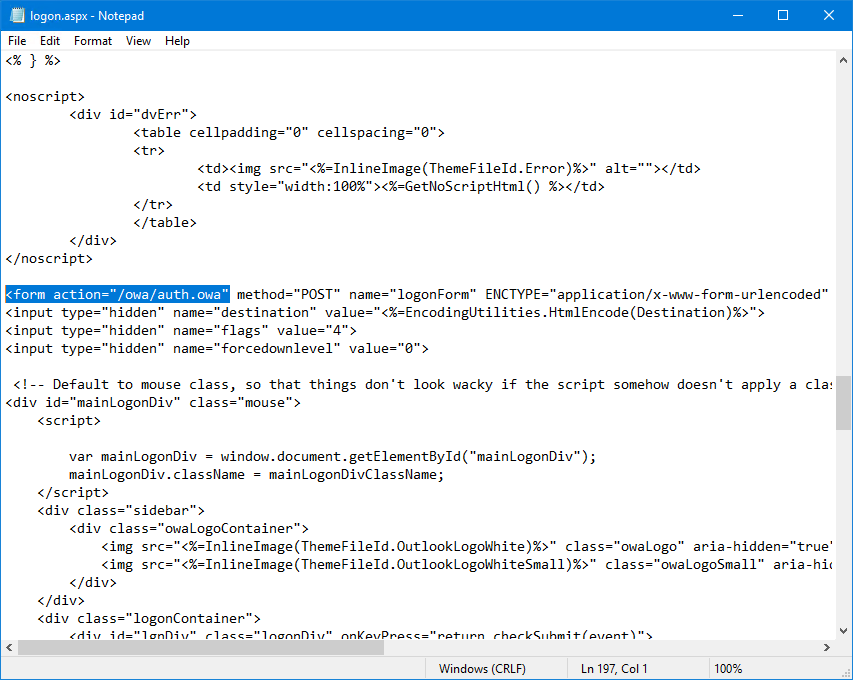
Change to:
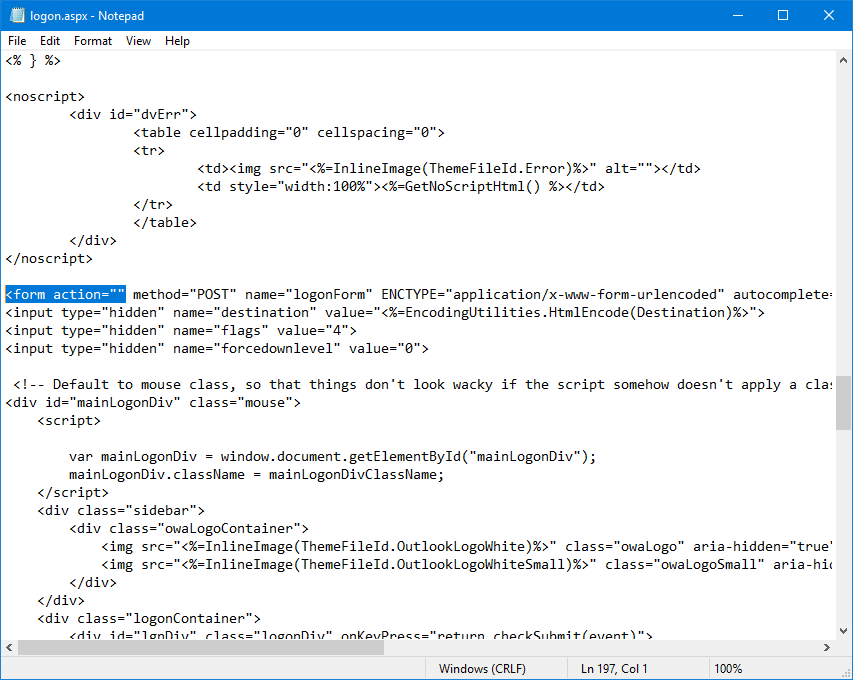
Find:
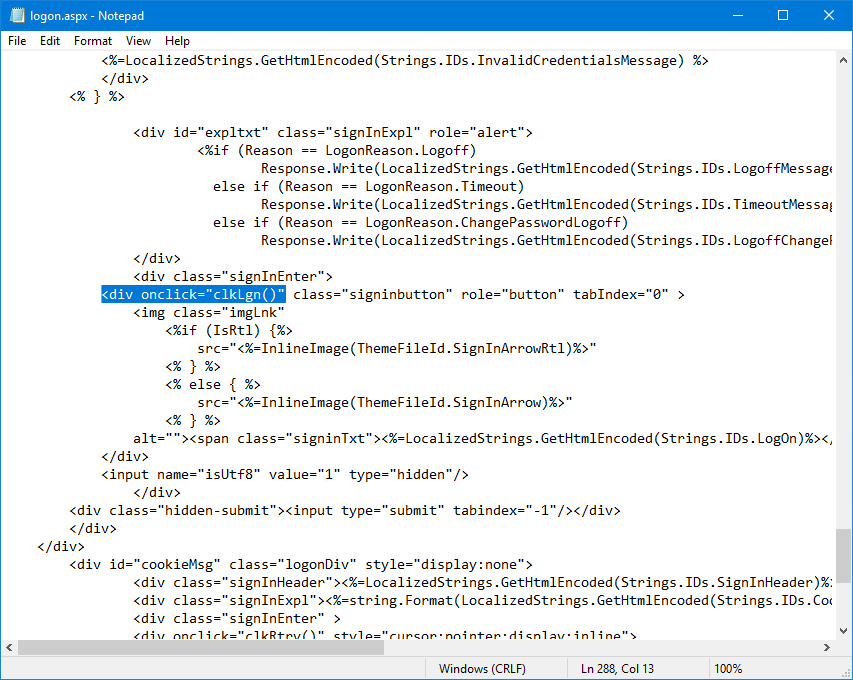
Change to:
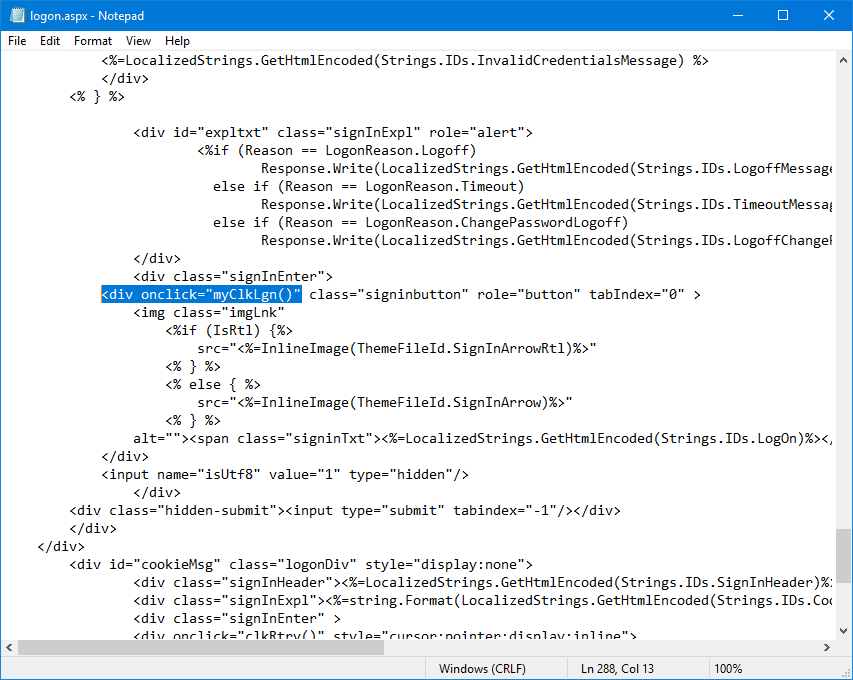
Find:
Next, press the Enter button and create a couple of empty lines.
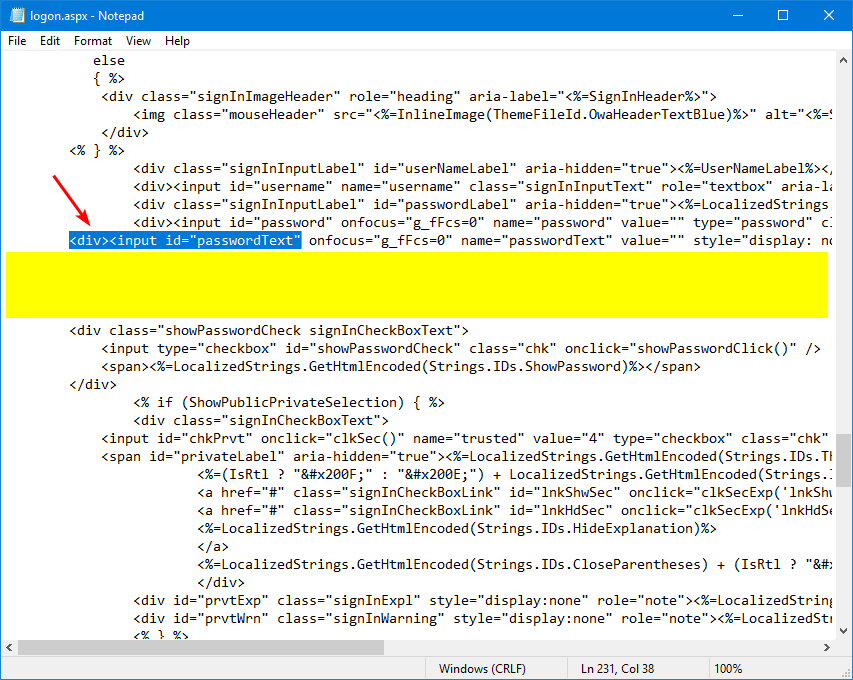
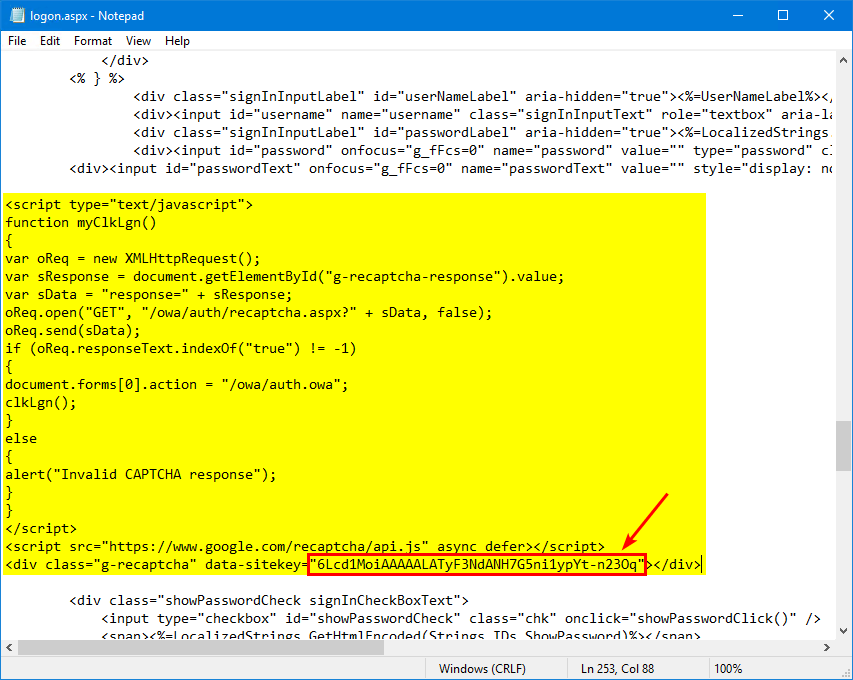
Copy/paste the below information into the empty lines.
Paste the Google reCAPTCHA site key you copied in the previous step and paste it in the field SITE_KEY.
Restart IIS on Exchange Server
You don’t need to restart IIS on the Exchange Server, and the Google reCAPTCHA will immediately appear on the Exchange Server OWA/ECP page.
Suppose it doesn’t, start Command Prompt as administrator and restart Internet Information Services (IIS) on the Exchange Server.
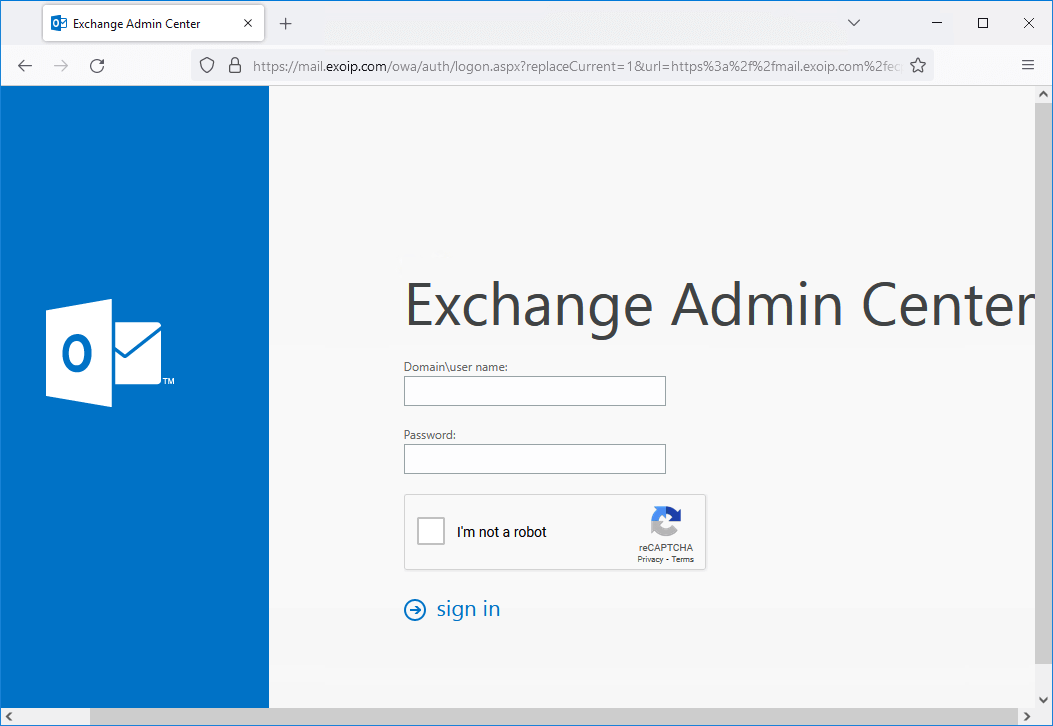
Verify Exchange Server OWA/ECP with Google reCAPTCHA
Start your favorite web browser and go to the Exchange Server OWA address.
The Google reCAPTCHA is visible.
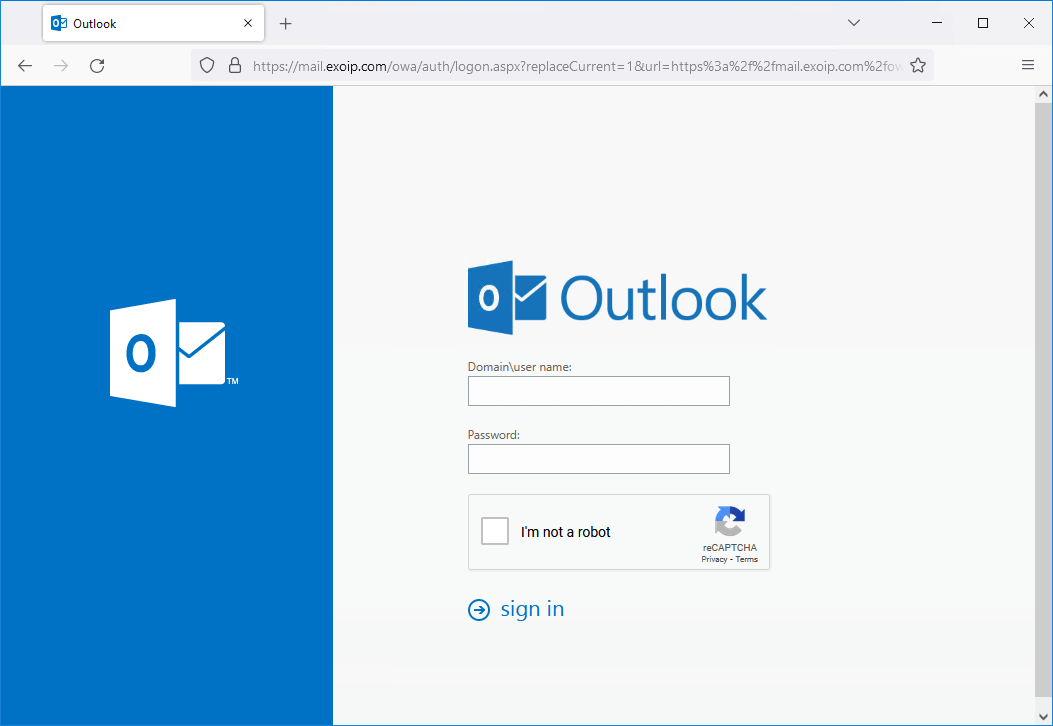
Fill in the user credentials and check the Google reCAPTCHA checkbox. Next, click on Sign in.
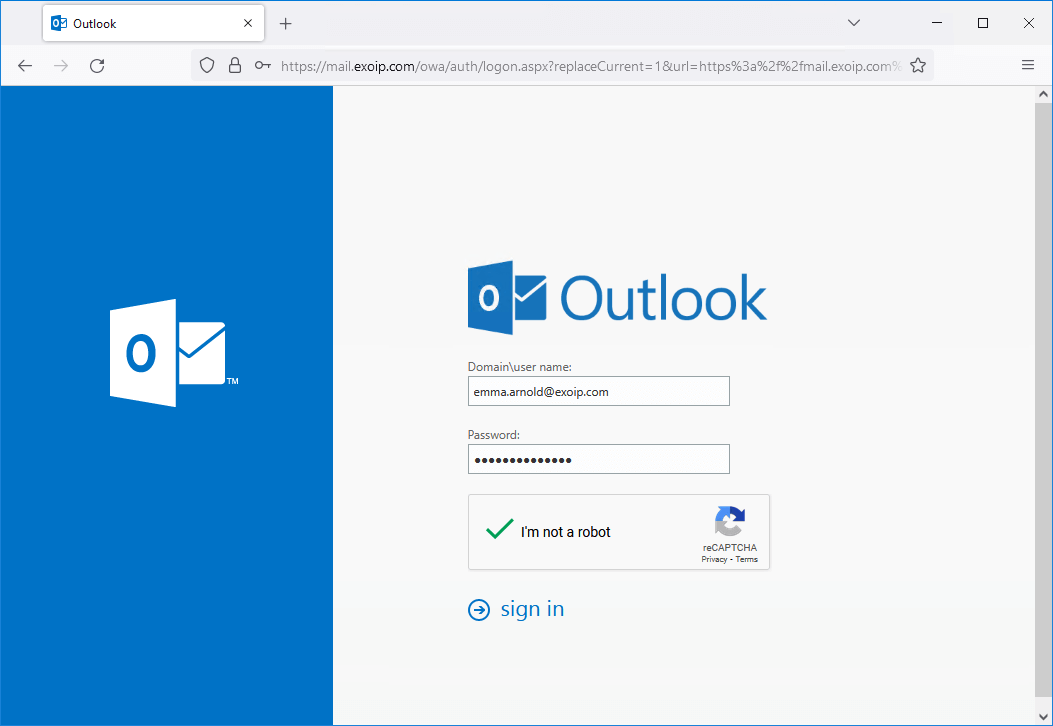
The user will successfully sign in.
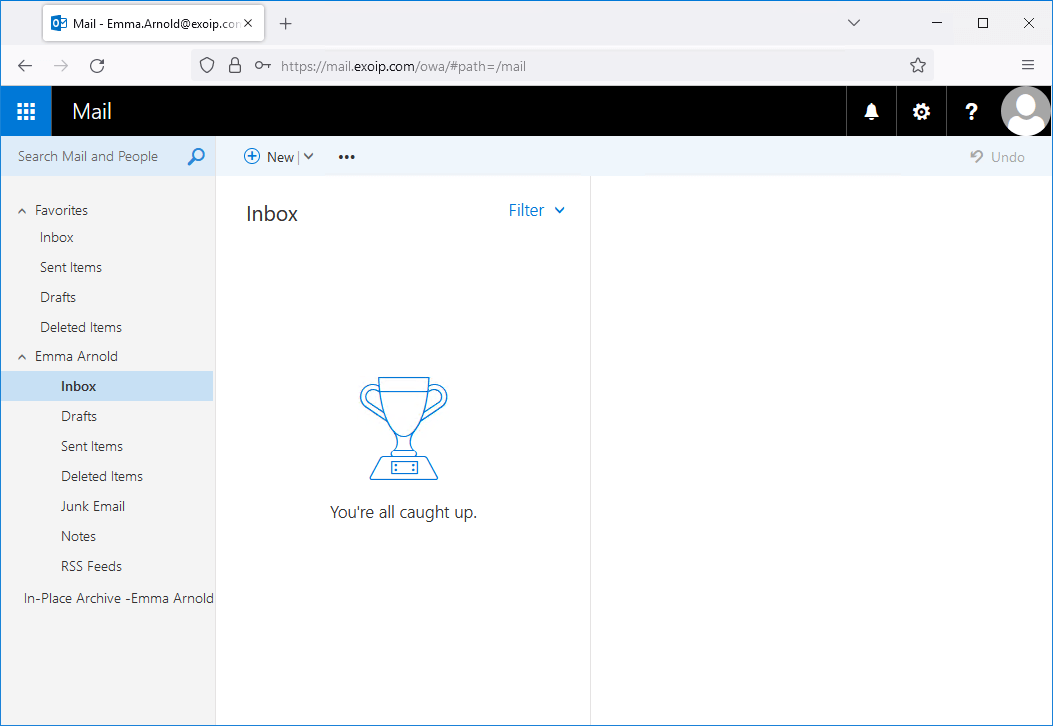
If the user fills in the wrong credentials, it will show the standard message: The user name or password you entered isn’t correct. Try entering it again.
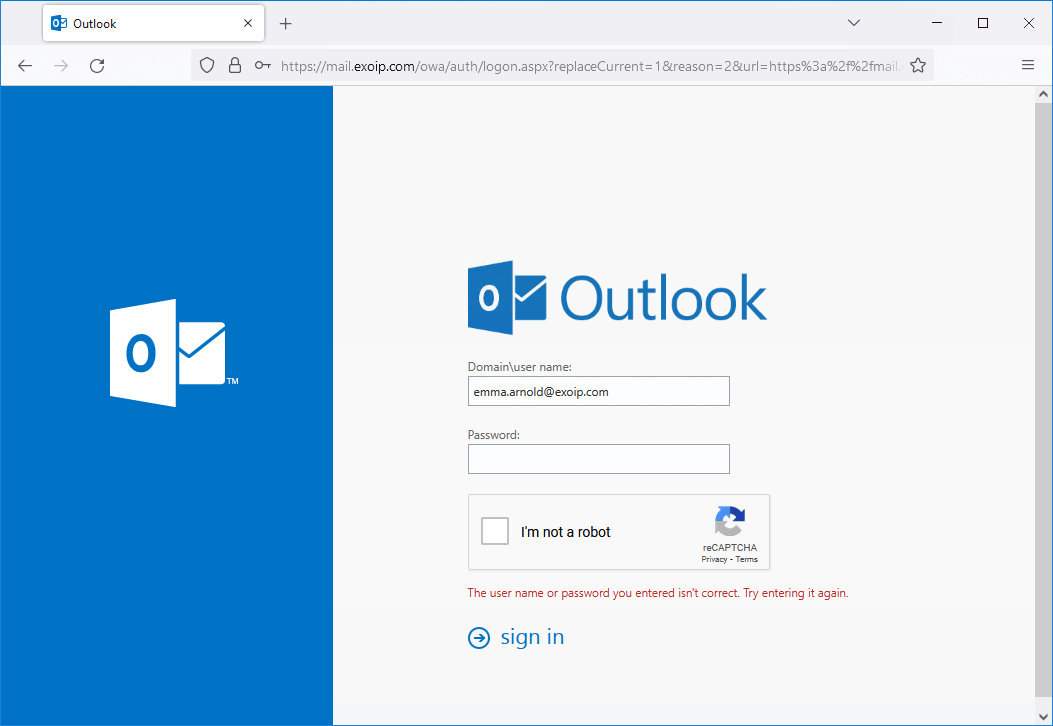
Suppose the user doesn’t accept the Google reCAPTCHA box and clicks on sign in. A message will appear with text: Invalid CAPTCHA response.
The same applies to the Exchange Admin Center (ECP) page.
It will also work when browsing to https://localhost/owa or https://localhost/ecp. That’s because you did add localhost in the first step when creating the site in Google reCAPTCHA.
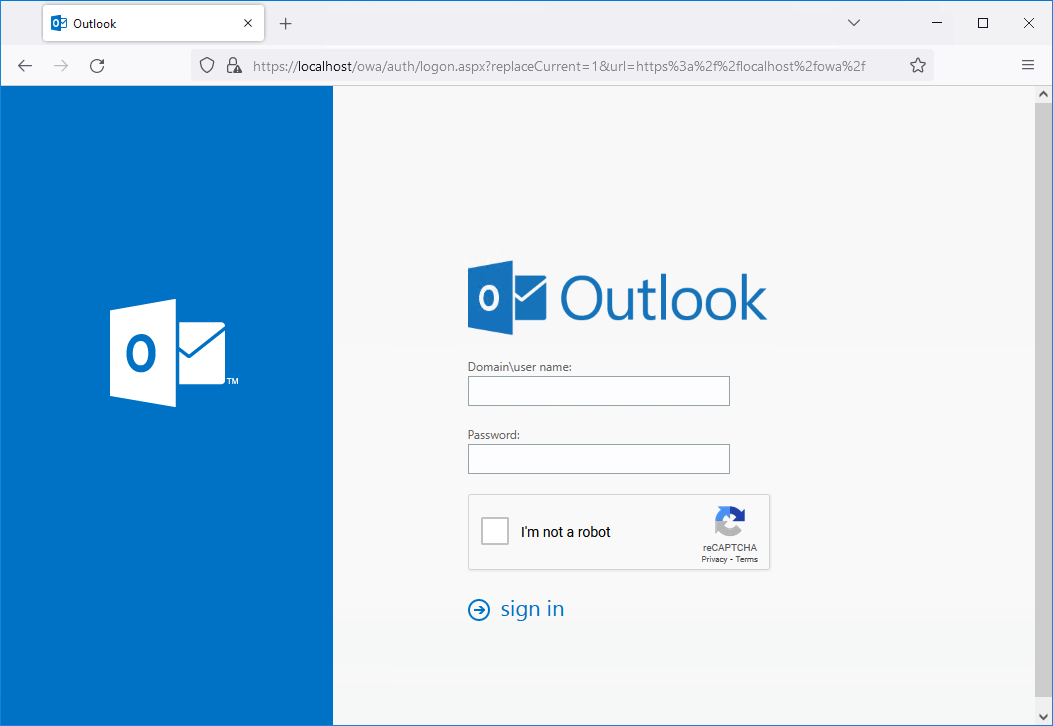
That’s it!
Read more: Secure Active Directory passwords from breaches »
Conclusion
You learned how to protect Exchange Server OWA/ECP from brute force attacks. First, create a free Google reCAPTCHA. After that, adjust the Exchange Server file so it will display and use the Google reCAPTCHA box on the OWA/ECP page. Combine this with an MFA solution, and you are good to go.
Did you enjoy this article? You may also like Disable external access to ECP in Exchange Server. Don’t forget to follow us and share this article.

Комментарии
Отправить комментарий